이 코스는 실제로 공개된 툴들을 사용하여 실제로 이벤트 수집과 분석, 머신 러닝 모델 구축이 가능한지에 대한 전반적인 지식을 전달하도록 설계되었습니다. 윈도우즈 머신의 이벤트 헌팅과 행위 정보 수집 등에 대해서도 다룹니다. 예제로 사용하는 Sysmon은 여러가지 제약에도 불구하고, 실제 기업 환경에서 실제적으로 사용되고 있습니다. 기본적으로 SIEM/EDR에 사용되는 여러 엔진들도 Sysmon의 개념에서 출발하므로 교육적인 목적으로 유용성이 많은 툴입니다. 고가의 EDR 등을 도입하기 힘든 경우 어떻게 실제 환경 구축이 가능하고, 어떠한 실질적인 제약이 있는지에 대해서도 다룹니다. 또한 개념상 SIEM과 EDR 등은 모두 비슷한 방법을 사용하여 이벤트 수집과 분석, 머신 러닝 단계로의 가공 작업이 이뤄지므로, SIEM/EDR/Threat Hunting과 같은 전반적인 개념을 공부하기에도 적당한 과정입니다.
트레이닝 기본 정보
| Name |
Details |
| Code |
599 |
| Title |
Malware Detection With Machine Learning |
| Level |
5 |
| Prerequisites |
ElasticSearch, 말웨어 행동에 대한 이해 |
| Days |
5 |
| Price |
440만원 (부가세 포함) |
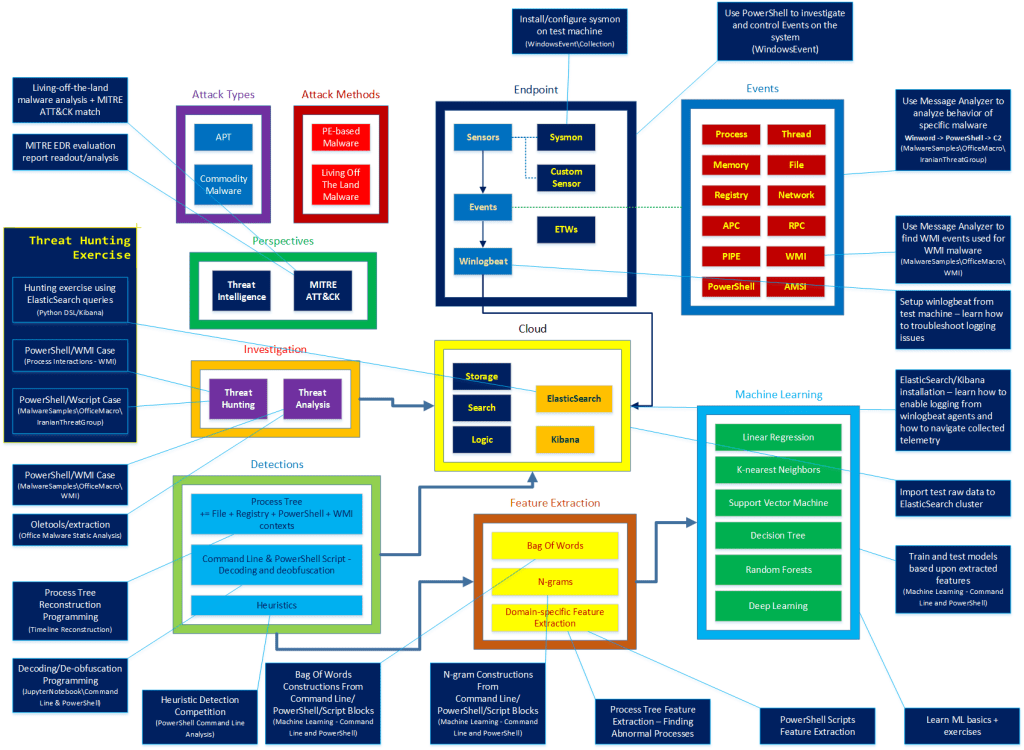
Chapter 1: APT/Threat Intelligence/MITRE ATT&CK Matrix/Threat Analysis
- Objectives:
- Understanding current APT landscape, Threat Intelligence
- Understanding threat modelling approach with MITRE ATT&CK Matrix
- Investigating real world malware/APT attacks and investigate and match them with MITRE ATT&CK Matrix for deeper understanding
| Session |
Duration |
Name |
Description |
| Session 1 |
0.5 hour |
Introduction |
Introduction, overview of the courses and exercise preparations |
| Session 1 |
0.3 hour |
Threat Intelligence |
APT vs Commodity Malware |
| Session 1 |
0.3 hour |
Threat Analysis |
PE vs Non-PE/Living-off-the-land Attacks |
| Session 1 |
0.3 hour |
Threat Modelling |
MITRE ATT&CK Matrix |
| Session 1 |
Homework |
Exercise |
Malware sample analysis |
Chapter 2: Endpoint - Windows Events/Telemetry Collection/Event Hunting
- Objectives:
- Understanding Windows Events collecting methods
- Learn using basic Windows Events tools (focusing on PowerShell cmdlets)
- Learning Windows Events hunting
- Based upon our knowledge on recent threat landscape, hunt for useful Windows events
| Session |
Duration |
Name |
Description |
| Session 2 |
2 hours |
Windows Events |
Windows Events - concepts and tools |
| Session 2 |
Homework |
Exercise |
Collect Windows events from test systems |
| Session 3 |
2 hours |
Advanced Windows Events |
PowerShell/WMI/Sysmon/AMSI |
| Session 3 |
Homework |
Exercise |
Run and analyze PowerShell malware with various sensors |
| Session 4 |
2 hours |
Exercise |
Windows Events Hunting & Investigations |
| Session 4 |
Homework |
Exercise |
Run various malware and find useful events |
Chapter 3: Cloud + Threat Hunting
- Objectives:
- Understanding cloud storage/distributed computing technology
- Acquiring and store telemetry data from Windows Events
- Performing threat hunting upon the collected telemetry data sets - understanding methodology and limitations
| Session |
Duration |
Name |
Description |
| Session 5 |
2 hours |
Cloud |
Introduction to various cloud storage and distributed processing platforms (Hadoop/Spark/Azure Data Lake/ElasticSearch/Kibana) |
| Session 5 |
Homework |
Exercise |
Use Hadoop/Spark/ADL for basic exercise |
| Session 6 |
2 hours |
Exercise |
Telemetry collections and threat hunting using ElasticSearch & Kibana - Setup ElasticSearch/Kibana environment/hunt threats |
| Session 6 |
Homework |
Exercise |
Use ES/Kibana installations and exercise various basic tools & queries |
Chapter 4: Heuristics
- Objectives:
- Understanding heuristics approach for malware/APT detections and limitations
- Introduction to data-scientific approach to real world problems
| Session |
Duration |
Name |
Description |
| Session 7 |
2 hours |
Data Science |
Machine Learning Algorithms |
| Session 7 |
Homework |
Exercise |
Exercise basic examples |
| Session 8 |
2 hours |
Exercise |
Timeline reconstruction (Python+Jupyter Notebook) |
| Session 8 |
Homework |
Exercise |
Construct timelines for various timeframe to find and analyze malicious actitivies |
| Session 9 |
2 hours |
Exercise |
Command line analysis |
| Session 9 |
Homework |
Exercise |
Build command line parser for basic analysis |
Chapter 5: Data Science
- Objectives:
- Applying various data science methodologies to security problems (focusing on the machine telemetry)
- Understanding importance of data clean-up
- Understanding process of feature set selections and extraction methods
| Session |
Duration |
Name |
Description |
| Session 10 |
2 hours |
Exercise |
Introduction to Machine Learning methods/concepts/exercise |
| Session 10 |
Homework |
Exercise |
Exercise basic data science examples |
| Session 11 |
2 hours |
Exercise |
Building Machine Learning Models |
| Session 11 |
Homework |
Exercise |
Exercise basic security data science examples |
| Session 12 |
2 hours |
Exercise |
Building Machine Learning Models |
| Session 12 |
Homework |
Exercise |
Exercise intermediate security data science examples |
등록 정보
